Can you tell me where this account is getting locked out from? is a frequent question that I would get often by Help Desk, or anyone in general; therefore, I decided to come up with a user-friendly Kibana dashboard where this information could be displayed.
This is an example of a dashboard that we can create once we have all the data we need.
Login Failure & Account Lockout
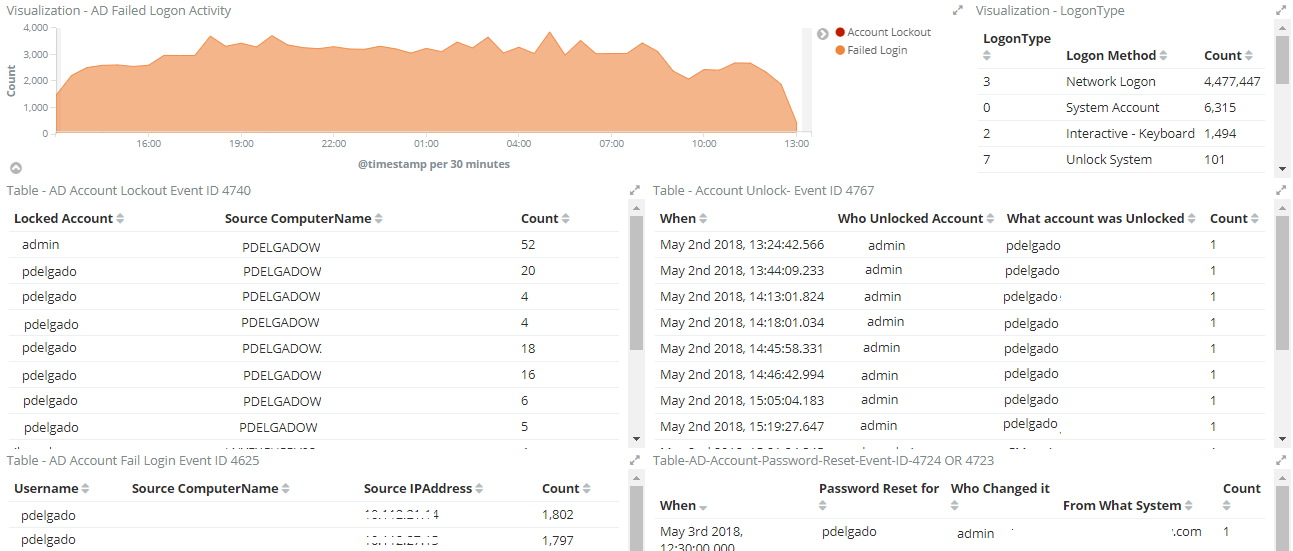
Overall login activity
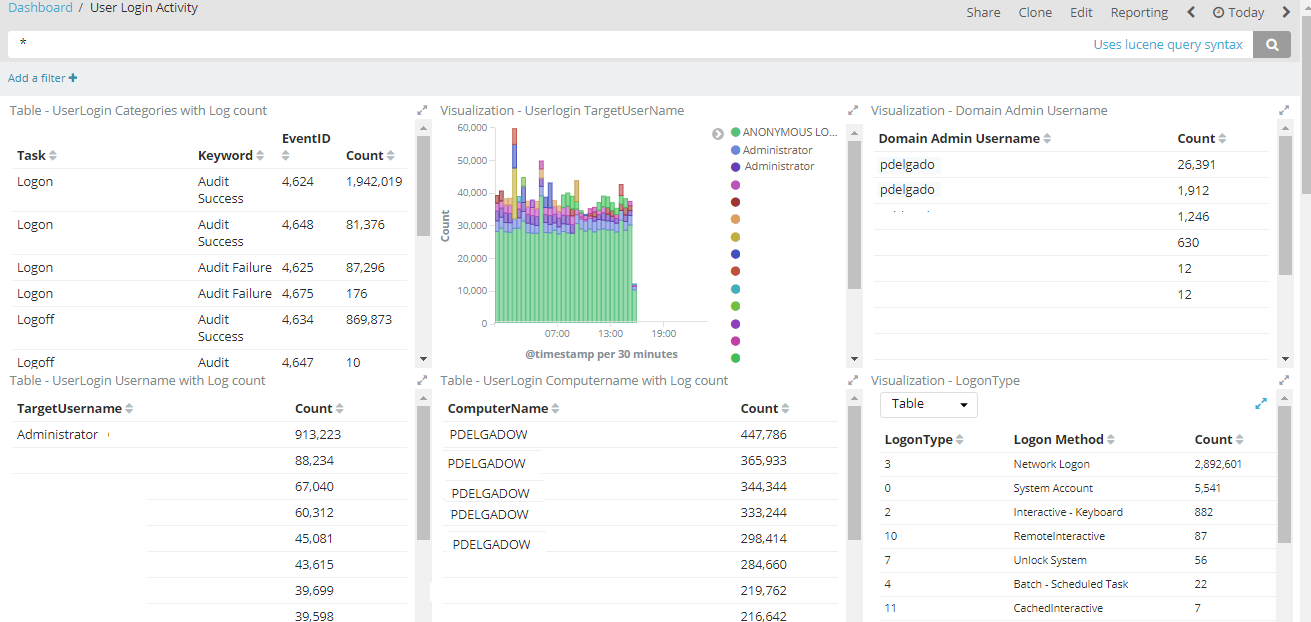
Our configuration will take care of the following:
- Remove the message field for certain event IDs such as Event ID 4625, or 4634 etc as the messages are long and repeat often which will impact your disk space. Besides you already have the fields you need to create your dashboard.
- Removes ::ffff from IP address fields. Sometimes certain IP fields will capture the data as :::ffff followed by the actual IP address, we want to display the IPV4 only.
- Adds context to event IDs that belong to Security Group Management Active Directory Login Types, and other Status messages related to accounts.
Here’s the Logstash configuration:
input {
beats {
port => 5050
tags => [ "winlogbeat" ]
}
}
# Removes ::ffff from IP address
filter {
if "winlogbeat" in [tags] {
mutate {
gsub => ["[event_data][IpAddress]", "::ffff:", ""]
}
}
}
#Active Directory Logon
filter {
if "winlogbeat" in [tags] and [log_name] == "Security" and [event_id] == 4624 or [event_id] == 4634 {
mutate {
remove_field => ["[message]"]
add_field => { "short_message" => "Logon Activity" }
}
}
}
#Active Directory Logon Failure
filter {
if "winlogbeat" in [tags] and [log_name] == "Security" and [event_id] == 4625 {
mutate {
remove_field => ["[message]"]
add_field => { "short_message" => "Logon Failure Activity" }
}
}
}
#Active Directory Logon - Event ID 4648 - A logon was attempted using explicit credentials.
filter {
if "winlogbeat" in [tags] and [log_name] == "Security" and [event_id] == 4648 {
mutate {
remove_field => ["[message]"]
add_field => { "short_message" => "A logon was attempted using explicit credentials" }
}
}
}
# Active Directory - Security Group Management
filter {
if "winlogbeat" in [tags] and [log_name] == "Security" and [event_id] == 4727 {
mutate {
add_field => { "short_message" => "A security-enabled global group was created" }
}
}
else if [event_id] == 4728 {
mutate {
add_field => { "short_message" => "A member was added to a security-enabled global group" }
}
}
else if [event_id] == 4729 {
mutate {
add_field => { "short_message" => "A member was removed from a security-enabled global group" }
}
}
else if [event_id] == 4730 {
mutate {
add_field => { "short_message" => "A security-enabled global group was deleted" }
}
}
else if [event_id] == 4731 {
mutate {
add_field => { "short_message" => "A security-enabled local group was created" }
}
}
else if [event_id] == 4732 {
mutate {
add_field => { "short_message" => "A member was added to a security-enabled local group" }
}
}
else if [event_id] == 4733 {
mutate {
add_field => { "short_message" => "A member was removed from a security-enabled local group" }
}
}
else if [event_id] == 4734 {
mutate {
add_field => { "short_message" => "A security-enabled local group was deleted" }
}
}
else if [event_id] == 4735 {
mutate {
add_field => { "short_message" => "A security-enabled local group was changed" }
}
}
else if [event_id] == 4737 {
mutate {
add_field => { "short_message" => "A security-enabled global group was changed" }
}
}
else if [event_id] == 4754 {
mutate {
add_field => { "short_message" => "A security-enabled universal group was created" }
}
}
else if [event_id] == 4755 {
mutate {
add_field => { "short_message" => "A security-enabled universal group was changed" }
}
}
else if [event_id] == 4756 {
mutate {
add_field => { "short_message" => "A member was added to a security-enabled universal group" }
}
}
else if [event_id] == 4757 {
mutate {
add_field => { "short_message" => "A member was removed from a security-enabled universal group" }
}
}
else if [event_id] == 4758 {
mutate {
add_field => { "short_message" => "A security-enabled universal group was deleted" }
}
}
else if [event_id] == 4764 {
mutate {
add_field => { "short_message" => "A group's type was changed" }
}
}
}
#Active Directory Login Types for Event id 4624,4634,4525
# Refence http://techgenix.com/logon-types/
filter {
if "winlogbeat" in [tags] and [log_name] == "Security" and [event_data][LogonType] == "2" {
mutate {
add_field => { "Method" => "Interactive - Keyboard" }
}
}
else if [event_data][LogonType] == "3" {
mutate {
add_field => { "Method" => "Network Logon" }
}
}
else if [event_data][LogonType] == "4" {
mutate {
add_field => { "Method" => "Batch - Scheduled Task" }
}
}
else if [event_data][LogonType] == "5" {
mutate {
add_field => { "Method" => "Service Account" }
}
}
else if [event_data][LogonType] == "7" {
mutate {
add_field => { "Method" => "Unlock System" }
}
}
else if [event_data][LogonType] == "8" {
mutate {
add_field => { "Method" => "NetworkCleartext" }
}
}
else if [event_data][LogonType] == "9" {
mutate {
add_field => { "Method" => "NewCredentials" }
}
}
else if [event_data][LogonType] == "10" {
mutate {
add_field => { "Method" => "RemoteInteractive" }
}
}
else if [event_data][LogonType] == "11" {
mutate {
add_field => { "Method" => "CachedInteractive" }
}
}
else if [event_data][LogonType] == "0" {
mutate {
add_field => { "Method" => "System Account" }
}
}
}
#Active Directory Login Types for Event id 4771,4776,4769,4768,
#Reference this https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventID=4776
filter {
if "winlogbeat" in [tags] and [log_name] == "Security" and [event_data][Status] == "0x0" {
mutate {
add_field => { "Statusmsg" => "Success" }
}
}
else if [event_data][Status] == "0x12" {
mutate {
add_field => { "Statusmsg" => "Account: disabled,expired,locked out,logon hours" }
}
}
else if [event_data][Status] == "0xB" {
mutate {
add_field => { "Statusmsg" => "Request start time is later than end time" }
}
}
else if [event_data][Status] == "0x17" {
mutate {
add_field => { "Statusmsg" => "Password has expired" }
}
}
else if [event_data][Status] == "0x18" {
mutate {
add_field => { "Statusmsg" => "Bad password" }
}
}
else if [event_data][Status] == "0x1b" {
mutate {
add_field => { "Statusmsg" => "Server principal valid for user-to-user only" }
}
}
else if [event_data][Status] == "0x1d" {
mutate {
add_field => { "Statusmsg" => "A service is not available." }
}
}
else if [event_data][Status] == "0x20" {
mutate {
add_field => { "Statusmsg" => "Ticket expired- Frequently logged by computer accounts" }
}
}
else if [event_data][Status] == "0x25" {
mutate {
add_field => { "Statusmsg" => "Workstation’s clock out of sync with the DC" }
}
}
else if [event_data][Status] == "0x6" {
mutate {
add_field => { "Statusmsg" => "Username does not exist or has not replicated" }
}
}
else if [event_data][Status] == "0xc000006a" {
mutate {
add_field => { "Statusmsg" => "Incorrect Password" }
}
}
else if [event_data][Status] == "0xc0000064" {
mutate {
add_field => { "Statusmsg" => "Username Does Not Exist" }
}
}
else if [event_data][Status] == "0xc0000072" {
mutate {
add_field => { "Statusmsg" => "Account is disabled" }
}
}
else if [event_data][Status] == "0xc0000234" {
mutate {
add_field => { "Statusmsg" => "Account is Locked Out" }
}
}
else if [event_data][Status] == "0xc0000193" {
mutate {
add_field => { "Statusmsg" => "Account Expiration" }
}
}
else if [event_data][Status] == "0xc000006f" {
mutate {
add_field => { "Statusmsg" => "Logon Outside Hours" }
}
}
else if [event_data][Status] == "0xc0000224" {
mutate {
add_field => { "Statusmsg" => "Use Required to change password next time" }
}
}
else if [event_data][Status] == "0xc0000071" {
mutate {
add_field => { "Statusmsg" => "Password expired" }
}
}
# related to event id: 4625
else if [event_data][Status] == "0xc000006d" {
mutate {
add_field => { "Statusmsg" => "Logon Failure" }
}
}
else if [event_data][Status] == "0xc000006e" {
mutate {
add_field => { "Statusmsg" => "Unknown user name or bad password." }
}
}
else if [event_data][Status] == "0xc000005e" {
mutate {
add_field => { "Statusmsg" => "No Logon Servers available to login" }
}
}
else if [event_data][Status] == "0xc0000133" {
mutate {
add_field => { "Statusmsg" => "Workstation’s clock out of sync with the DC" }
}
}
else if [event_data][Status] == "0xc00002ee" {
mutate {
add_field => { "Statusmsg" => "An Error occured during Logon" }
}
}
else if [event_data][Status] == "0xc000015b" {
mutate {
add_field => { "Statusmsg" => "Login Not Allowed for this system" }
}
}
else if [event_data][Status] == "0xc0000225" {
mutate {
add_field => { "Statusmsg" => "Windows Bug and not a risk" }
}
}
}
######################### End of Active Directory Security Logs ############################
output {
if "winlogbeat" in [tags] and [log_name] == "Security" {
elasticsearch {
hosts => ["http://yoursecuritylogselk:9200"]
index => "logstash-winsecurity-%{+xxxx.ww}"
}
}
# old index format: index => "logstash-winlogbeat-%{+YYYY.MM.dd}"
else if "winlogbeat" in [tags] {
elasticsearch {
hosts => ["http://yourelk:9200"]
index => "logstash-winlogbeat-%{+xxxx.ww}"
}
}
}
The configuration above sends all Security-related logs to it’s own Elasticsearch server and the rest to another server, you may change the output as you like.
Here’s some basic steps on creating a Failed Login visualization:
On Kibana Navigate to Visualize > Create New visualization > Select Data Table and select your index.
type: event_id: 4625 and add the following fields:
- event_data.TargetUserName.keyword = Username
- event_data.WorkstationName.keyword = Source Computername
- event_data.IpAddress.keyword = Source IPAddress
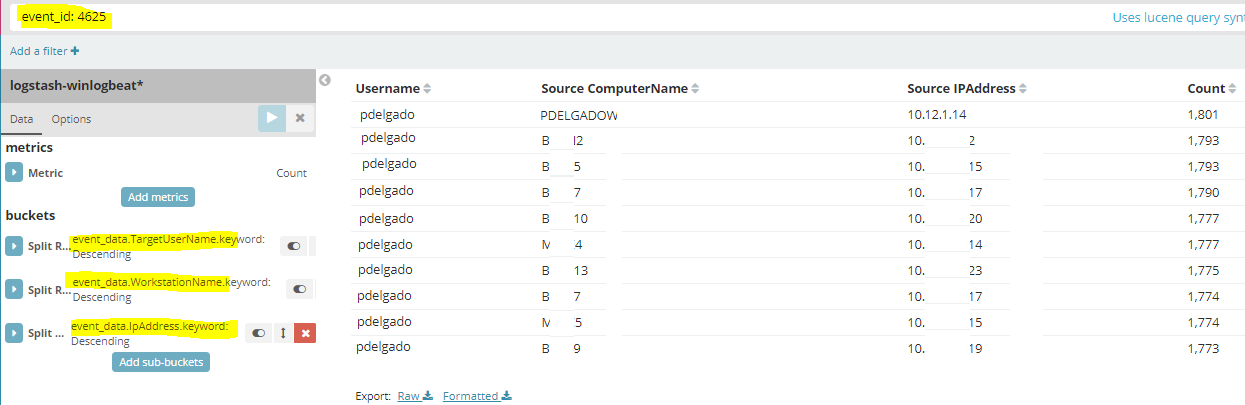
Generate and save your visualization.
You should be able to create other dashboards that satisfy what you are looking for to ensure you are monitoring your environment.
Other suggested dashboards include:
- Account Creation
- Account Disabling & Deletion
- Account Password Reset
- Kerberos Connections – Such as SMB
- Security Group Management
Thanks for reading!
Since you read this far……
These are the Security-related Event IDs that I’m capturing from most generated to least generated events:
| EventID | Log Name | Keyword |
| 4,624 | Logon | Audit Success |
| 4,634 | Logoff | Audit Success |
| 4,776 | Credential Validation | Audit Success |
| 4,769 | Kerberos Service Ticket Operations | Audit Success |
| 4,648 | Logon | Audit Success |
| 4,625 | Logon | Audit Failure |
| 5,140 | File Share | Audit Success |
| 4,771 | Kerberos Authentication Service | Audit Failure |
| 4,768 | Kerberos Authentication Service | Audit Success |
| 4,776 | Credential Validation | Audit Failure |
| 4,673 | Sensitive Privilege Use | Audit Failure |
| 4,672 | Special Logon | Audit Success |
| 4,768 | Kerberos Authentication Service | Audit Failure |
| 5,145 | Detailed File Share | Audit Success |
| 4,656 | File System | Audit Success |
| 5,136 | Directory Service Changes | Audit Success |
| 4,663 | File System | Audit Success |
| 4,770 | Kerberos Service Ticket Operations | Audit Success |
| 4,769 | Kerberos Service Ticket Operations | Audit Failure |
| 6,281 | System Integrity | Audit Failure |
| 4,674 | Sensitive Privilege Use | Audit Success |
| 4,931 | Detailed Directory Service Replication | Audit Success |
| 4,957 | MPSSVC Rule-Level Policy Change | Audit Failure |
| 4,673 | Sensitive Privilege Use | Audit Success |
| 5,038 | System Integrity | Audit Failure |
| 4,656 | Kernel Object | Audit Success |
| 4,702 | Other Object Access Events | Audit Success |
| 4,663 | Kernel Object | Audit Success |
| 4,719 | Audit Policy Change | Audit Success |
| 4,691 | Other Object Access Events | Audit Success |
| 4,780 | User Account Management | Audit Success |
| 4,656 | Removable Storage | Audit Success |
| 4,740 | User Account Management | Audit Success |
| 4,656 | Registry | Audit Success |
| 4,663 | Removable Storage | Audit Success |
| 4,674 | Sensitive Privilege Use | Audit Failure |
| 4,985 | File System | Audit Success |
| 4,675 | Logon | Audit Failure |
| 4,656 | SAM | Audit Success |
| 4,928 | Detailed Directory Service Replication | Audit Failure |
| 4,738 | User Account Management | Audit Success |
| 4,660 | File System | Audit Success |
| 4,742 | Computer Account Management | Audit Success |
| 4,907 | Audit Policy Change | Audit Success |
| 4,723 | User Account Management | Audit Success |
| 4,735 | Security Group Management | Audit Success |
| 4,724 | User Account Management | Audit Success |
| 4,904 | Audit Policy Change | Audit Success |
| 4,905 | Audit Policy Change | Audit Success |
| 5,137 | Directory Service Changes | Audit Success |
| 4,723 | User Account Management | Audit Failure |
| 4,664 | File System | Audit Success |
| 4,755 | Security Group Management | Audit Success |
| 4,757 | Security Group Management | Audit Success |
| 4,660 | Kernel Object | Audit Success |
| 4,611 | Security System Extension | Audit Success |
| 5,061 | System Integrity | Audit Success |
| 4,760 | Distribution Group Management | Audit Success |
| 4,767 | User Account Management | Audit Success |
| 5,058 | Other System Events | Audit Success |
| 5,141 | Directory Service Changes | Audit Success |
| 4,647 | Logoff | Audit Success |
| 4,762 | Distribution Group Management | Audit Success |
| 6,144 | Other Policy Change Events | Audit Success |
| 5,140 | File Share | Audit Failure |
| 4,722 | User Account Management | Audit Success |
| 6,416 | Plug and Play Events | Audit Success |
| 4,725 | User Account Management | Audit Success |
| 4,756 | Security Group Management | Audit Success |
| 4,779 | Other Logon/Logoff Events | Audit Success |
| 4,622 | Security System Extension | Audit Success |
| 4,625 | Account Lockout | Audit Failure |
| 4,720 | User Account Management | Audit Success |
| 4,761 | Distribution Group Management | Audit Success |
| 4,778 | Other Logon/Logoff Events | Audit Success |
| 4,656 | Removable Storage | Audit Failure |
| 4,656 | File System | Audit Failure |
| 4,800 | Other Logon/Logoff Events | Audit Success |
| 5,139 | Directory Service Changes | Audit Success |
| 4,659 | File System | Audit Success |
| 4,732 | Security Group Management | Audit Success |
| 4,728 | Security Group Management | Audit Success |
| 5,145 | Detailed File Share | Audit Failure |
| 4,656 | Kernel Object | Audit Failure |
| 4,724 | User Account Management | Audit Failure |
| 4,801 | Other Logon/Logoff Events | Audit Success |
| 4,698 | Other Object Access Events | Audit Success |
| 4,699 | Other Object Access Events | Audit Success |
| 4,716 | Authentication Policy Change | Audit Success |
| 4,737 | Security Group Management | Audit Success |
| 4,802 | Other Logon/Logoff Events | Audit Success |
| 4,803 | Other Logon/Logoff Events | Audit Success |
| 4,701 | Other Object Access Events | Audit Success |
| 4,781 | User Account Management | Audit Success |
| 4,954 | MPSSVC Rule-Level Policy Change | Audit Success |
| 1,100 | Service shutdown | Audit Success |
| 4,608 | Security State Change | Audit Success |
| 4,610 | Security System Extension | Audit Success |
| 4,614 | Security System Extension | Audit Success |
| 4,726 | User Account Management | Audit Success |
| 4,902 | Audit Policy Change | Audit Success |
| 5,056 | System Integrity | Audit Success |
| 4,733 | Security Group Management | Audit Success |
| 4,764 | Security Group Management | Audit Success |
| 4,946 | MPSSVC Rule-Level Policy Change | Audit Success |
| 4,947 | MPSSVC Rule-Level Policy Change | Audit Success |
| 4,948 | MPSSVC Rule-Level Policy Change | Audit Success |
Hello Pablo,
very nice works, I’ll try to take some of your suggestions.
I was testing your config and I just want to advise you that you forgot a “}” to close the else if:
else if [event_data][LogonType] == “9” {
mutate {
add_field => { “Method” => “NewCredentials” }
}
thanks again,
Cesare
Thanks for catching that, it’s been updated!
Pablo, you would mind to share your config files? I´ve tried to make it work but far from it.
Thanks for your attention.
That Logstash configuration should work. Are you getting an error message or anything?
Hi Pablo, I finally got to work 🙂
Would you mind to share your dashboard files?!
Thanks
Unfortunately I don’t have the files accessible anymore because of my test environment, did you need ideas or field names to use?
I am unable to make two indexes using your logstash conf, one for windows and one for security , I am using logstash 7.3 , Please help me out for this
Can you please share the config files ?
The one I shared is the logstash config file. Are you referring to a different one?
I am running all ELK stack on one Ubuntu server. I am looking for logstack files and elasticstach, filebeat.yml files.
Here’s a quick guide for Winlogbeat (yml) https://www.syspanda.com/index.php/2017/02/07/setting-up-elasticsearch-5-x-sending-windows-logs-using-winlogbeat-5-x/
Logstash one you can see it on this article (save it as .conf).
I am using winlogbeats on my windows servers to send the logs to lagstash output. I am using 02-beats-input.conf, 10-syslog-filter.conf and 30-elasticsearch-output.conf. How should I use your code file name in my case ? Should I use 11-ad-monitoring.conf or just ad-monitoring.conf ? These files are saved in /etc/logstash/conf.d folder. Please advice
Please share logstash file, my fields for filters are not working, all data is coming with winlogbeat.event_id etc , but when I try to filter and add fields, it is not working. Also I am unable to make separate index for Security and other windows logs
I am using winlogbeats on my windows servers to send the logs to lagstash output. I am using 02-beats-input.conf, 10-syslog-filter.conf and 30-elasticsearch-output.conf. How should I use your code file name in my case ? Should I use 11-ad-monitoring.conf or just ad-monitoring.conf ? These files are saved in /etc/logstash/conf.d folder. Please advice
How do we send the logs from active directory that exists on premise to winlogbeat that exists on aws cloud?
Hey this is a beautiful article. I am just getting started with ELK. I am trying out 7.8 right now. So by default in /etc/logstash/conf.d folder I have one logstash.conf file with no filter.
Should I create another conf file with the input, filter, and output section?, while input section pointing to 5044 the default logstash port.
[…] Monitoring Active Directory with ELK – Syspanda […]