At this point you have tightened up your environment by removing local administrator rights, keeping up your software up-to-date, blocking 3rd party software download sites, etc. etc…; however, you start seeing some traffic going to a 3rd party converter site, or worse, some nasty Adware site. Since you’re logging everything in your environment, naturally you search to see what applications are making these connections outbound, but nothing, nada!
You keep looking and find out these outbound connections are going to hmyquickconverter.com
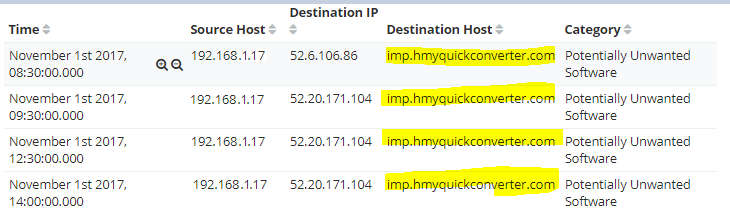
After doing some online research, you realize this is a browser extension and now know where to look. Let’s hunt for these extensions!
Side note: it is a known fact that browser extensions have been getting hijacked by malicious actors and are being used for nefarious purposes. In case you needed more reasons to take action!
Let the hunting begin
Since we’re collecting Sysmon logs we can do a quick search for extensions by running the following queries on Kibana
"Default\\Extensions\\"
Alternatively you can also run the following which will return a handful of add-ons such as Adobe Reader, Webex, etc. etc..
event_data.ParentCommandLine: "chrome.exe" AND "chrome-extension:"
The first query returns the following:
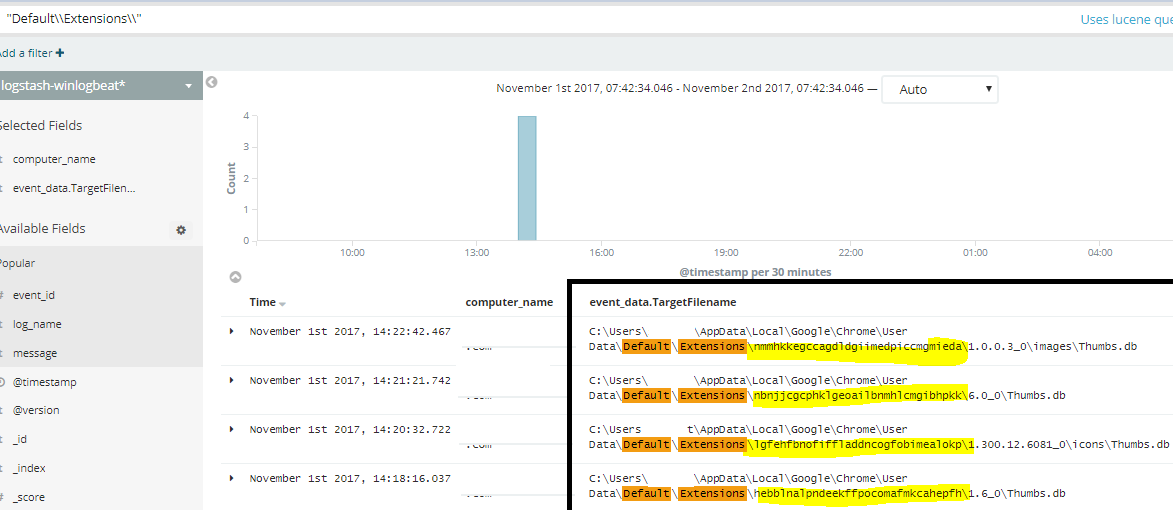
A closer look at these browser extensions:
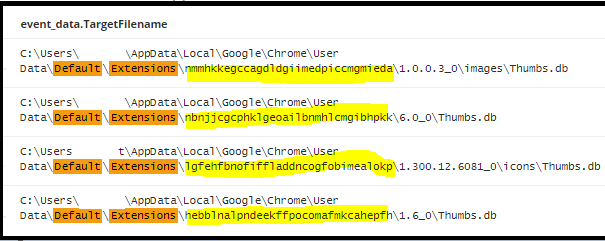
Identifying these browser extensions:
- Google Chrome Web Store: nmmhkkegccagdldgiimedpiccmgmieda
- My Quick Converter (Adware): nbnjjcgcphklgeoailbnmhlcmgibhpkk
- ASK Toolbar: lgfehfbnofiffladdncogfobimealokp
- Tracker Package: hebblnalpndeekffpocomafmkcahepfh
You can then browse to the offending machine and browse the following path to see what other extensions are found:
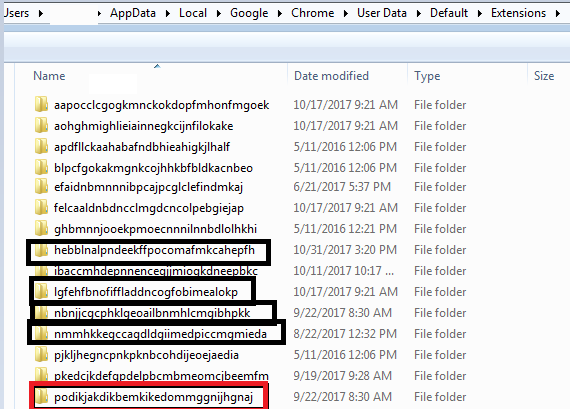
The location of these extensions are usually here: C:\Users\user\AppData\Local\Google\Chrome\User Data\Default\Extensionefaidnbmnnnibpcajpcglclefindmkajs
Found an additional one (Red):
- Search encrypt (Adware): podikjakdikbemkikedommggnijhgnaj
So great, now you can have your staff remove these browser extensions and possibly uninstall google chrome; however, this doesn’t resolve the problem. Next week you’ll continue seeing other 3rd party extensions that your users will install to bypass your security.
Solution
Google Chrome can be managed through Group Policy; therefore, we can set it up in order to blacklist all extensions and only approved trusted ones like adobe reader, webex, your AV browser extension, and other approved ones that your company needs.
Here’s an article that explains how to setup the GPO so I won’t cover that.
Once you set it up, you can Blacklist all extensions and white-list specific ones by performing the following:
- Right click your computer OU and
- Create GPO in this domain, and link it here
- Provide a name (Chrome Corporate Settings) , click OK
- Right click your newly created GPO “Chrome Corporate Settings” and select Edit
- Navigate to Computer Configuration > Policies > Administrative Template > Google Chrome > Extensions
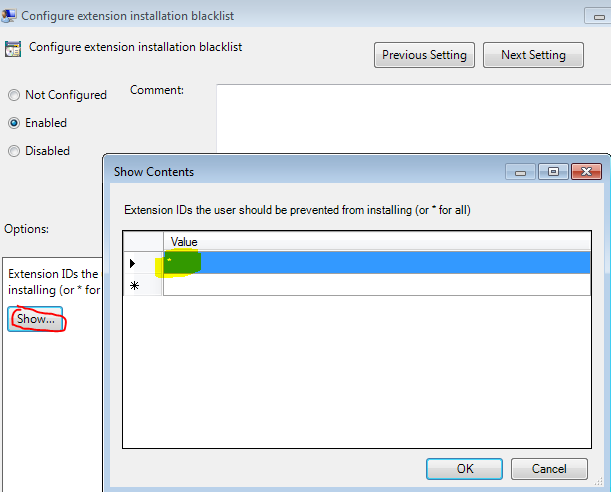
- Double-Click on Configure extension installation blacklist and Enable.Next, click on Show, You will then type an asterisk “*” (no quotes), to ensure all extensions are blocked.
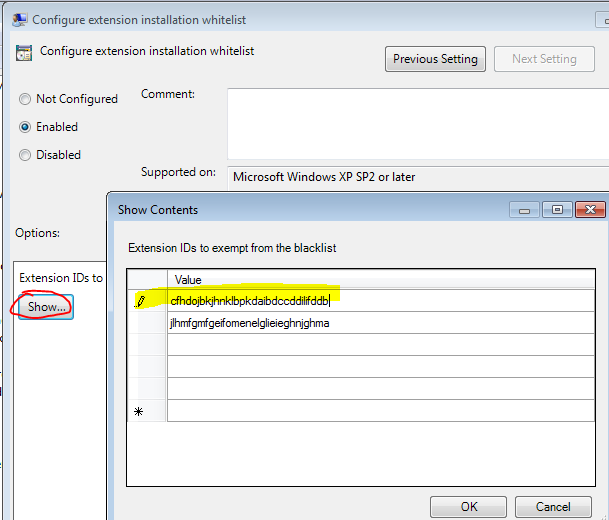
- Double-click on Configure extension installation whitelist and enable. Next, click on Show, You will then enter the Extension ID of your approved extensions: Example AdblockPlus is: cfhdojbkjhnklbpkdaibdccddilifddb
- Done!
Now go and test some endpoints to ensure that this is being applied.
Now when attempting to install a new extension, your users will get the following:
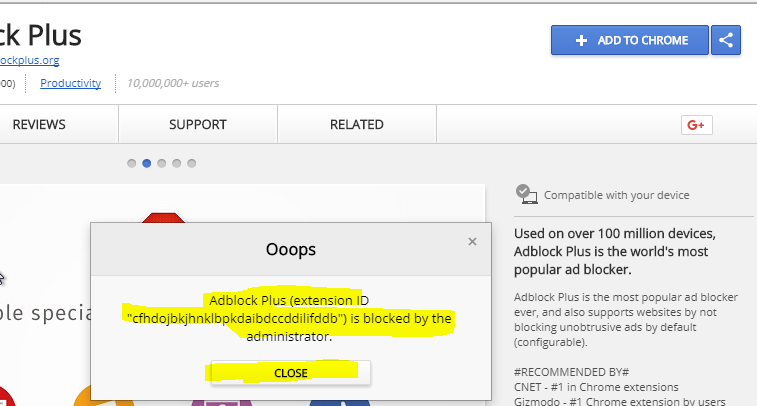
Additionally, any existing extensions that are not white-listed, will no longer work which is perfect for our use case.
Moving forward
Remember that once you enable this GPO, many extensions won’t work. Since there might be some extensions needed, ensure that you do your due diligence by finding this information. Obviously, if you are collecting logs, you won’t have to wait for an upset business user to ask why they can’t do their webex anymore; therefore, we go back to our search queries:
"chrome-extension:"
Here’s some results:
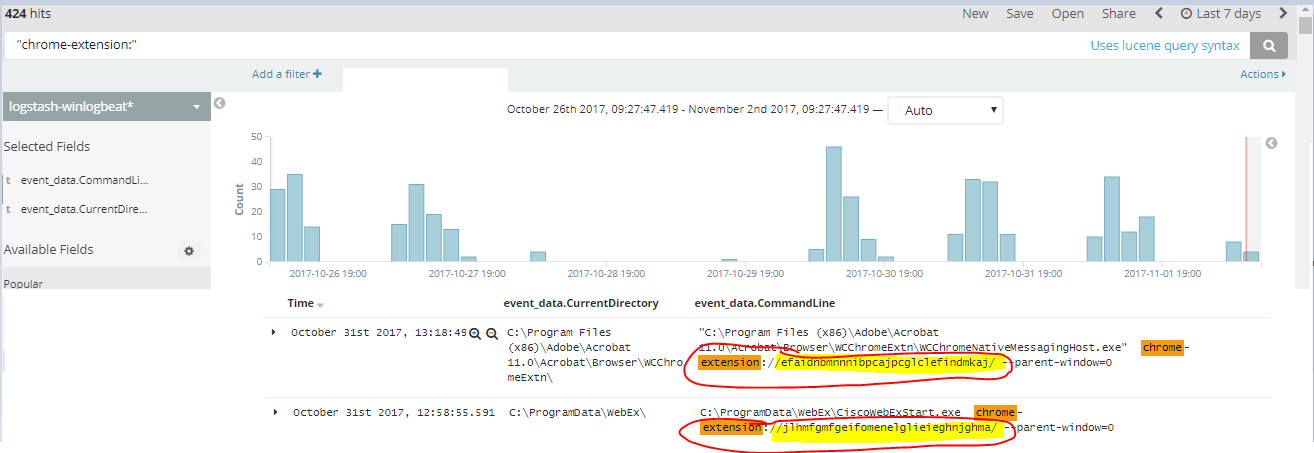
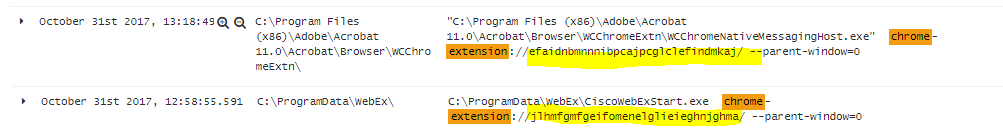
Here’s some of the common ones used in most environments:
- Adobe Acrobat – efaidnbmnnnibpcajpcglclefindmkaj
- Cisco Webex Extension – jlhmfgmfgeifomenelglieieghnjghma
- ICloud Bookmarks – fkepacicchenbjecpbpbclokcabebhah
- Dashlane (Password manager) – fdjamakpfbbddfjaooikfcpapjohcfmg
- Adobe Reader:efaidnbmnnnibpcajpcglclefindmkaj
- Google docs: ghbmnnjooekpmoecnnnilnnbdlolhkhi
- Google search: coobgpohoikkiipiblmjeljniedjpjpf
- Google Drive: apdfllckaahabafndbhieahigkjlhalf
- Youtube: blpcfgokakmgnkcojhhkbfbldkacnbeo
- Gmail: pjkljhegncpnkpknbcohdijeoejaediaibaccmhdepnnencegjjmiogkdneepbkc
- Google slides: aapocclcgogkmnckokdopfmhonfmgoek
- Google docs: aohghmighlieiainnegkcijnfilokake
- Google sheets: felcaaldnbdncclmgdcncolpebgiejap
- McAfee Site Advisor: cmendinpapjjojakimjlmkkkcmnojefg
- Chromcas? : pkedcjkdefgpdelpbcmbmeomcjbeemfm
- Google Chrome Web Store: nmmhkkegccagdldgiimedpiccmgmieda
Others (Just for reference):
Tracker Package: hebblnalpndeekffpocomafmkcahepfh
ASK Toolbar: lgfehfbnofiffladdncogfobimealokp
My Quick Converter: nbnjjcgcphklgeoailbnmhlcmgibhpkk
Search encrypt (Adware): podikjakdikbemkikedommggnijhgnaj
Final Thoughts:
This Chrome GPO has many other options to customize chrome so make sure you go through the settings thoroughly if you want to make further customization.
Side note: Users will install VPN or remote utilities through browser extensions so be very, very careful! And as always, don’t underestimate your business users as they will always find a way to bypass your security.
Update: 8-07-2018
I had previous classified nmmhkkegccagdldgiimedpiccmgmieda as Adware; however, I realized this is Google Web Store.
In addition, I wrote another article on Identifying and removing unwanted Google Chrome extensions through powershell which may be accessed here.
[…] For this particular use case, we’re trying to identify what Chrome extensions are installed in our non-domain endpoints that we’re managing. If you are dealing with domain-joined systems, I’d recommend managing these extensions via Google Chrome’s GPO which can be found in my past article. […]