If you find yourself responding to daily incidents such as having to remove adware from a system, or having to run a powershell script to delete user emails because of phishing emails, you might think that this is all part of the daily struggles any Security person goes through; however, what if I told you this could stop and you could focus on bigger and better things for your organization?
First, ask yourself how does this adware or malware gets to your systems initially? Are there that many 0-days in the wild that our company just doesn’t stand a chance? or perhaps it’s as simple as one of your HR folks trying to download a 3rd party audio editing software to compile a list of Halloween songs. From my experience, it’s the latter.
Enter the Human
Humans are complex individuals with varying emotions, and psychology plays a lot in our everyday lives. Malicious actors are great social engineers (some of them), and understand that humans in organizations are the weakest links. Understanding this fact allows them to exploit this vulnerability by targeting companies with phishing emails that prompt the human to take a specific action (whether it’s click on an email attachment, link, or money wire transfer). Your fancy “next-next-next-gen” endpoint protection, or futuristic sand-boxing technologies won’t protect you against this! Know this for a fact and challenge your vendors!
I’m willing to bet many of you spend quite a bit of your time performing the following:
- Writing complex regex queries to catch certain emails
- Blacklisting email addresses (Which is never ending!)
- Updating your SRP notification policies to include the latest ransomware extension
- Blocking individual C&C URLs that your web protection didn’t catch
- [insert your daily actions here]
Understanding that putting out fires is not the best use of your 8-hour workday, we have to tackle what should really matter here which is Employee Security Awareness training.
Investing in your Human defense: Education
Security awareness training should be a major point of conversation when talking about your company’s security program. If this is not the case, then you should not be in security, period! Humans are your real-time sensors that are able to catch things that your IPS/HIDS are not able to since we’re good at catching anomalies. Don’t underestimate your people (young or old) and instead focus on educating them as you’ll be updating their powerful brain engines to detect suspicious behavior.
I get the point now, so how do I get started?
Before you get started with your PowerPoint presentation, here’s what you should ask yourself first:
- What message am I trying to get across? Basically at the end of the day what do I want my employees to leave with. This is very important as many people have different reasons for attending your security presentation in the first place. I wanted the employees to be extra aware of phishing emails as that’s our #1 attack vector, and also understand that their actions have real financial consequences.
- How long do I want my presentation to be? Your presentation should be optimal in time; however, personally I found that 30-45 minutes worked well for me. I added a Phishing Quiz around minute 25 which allowed the audience to relax a bit and be engaged before continuing with the 2nd part of the presentation.
Security Awareness: Topics
The following is a list of topics to be covered (recommended):
- Basic terminology (What is Security,Confidentiality, Integrity, Availability, and Privacy).
- Sensitive Data– Specially if your company has certain regulations or needs to adhere to certain standards. (PII, PCI, HIPAA,etc)
- Cost of breaches – Make your employees understand that there is financial gains and losses from these breaches.
- Data has monetary value for someone out there.
- Provide personal examples that relate to them (Fraud, Identity theft, Credit card theft)
- Examples of breaches– Specially those in your same sector or companies that your employees are familiar with
- Cost of stolen records (Credit cards, Patents, Proprietary data)
- Breach Facts
- Insiders are the most likely perpetrators
- Average time to detect a breach
- Majority of breaches leverage a weak,default,stolen password
- How to protect your company
- User Login & Practices
- Passwords practices
- Secure Backups
- Email Usage
- Attacks – Targeted attacks
- Spear Phishing emails
- Malicious attachments – (Watch for Enabling macros)
- Holidays – When we’re most vulnerable
- What to look for
- Tone of emails (Urgent, Angry)
- Attachments and non-familiar extensions
- Other types of Phishing
- Vishing
- Whaling
- Other Threats
- Ransomware
- Malware
- Spear Phishing emails
- Phishing Quiz – Interactive Phishing Quiz
- Physical Security
- Not sharing employee badges
- Escorting visitors & vendors in and out
- PIN codes for mobile devices
- Locking computers after stepping away
- USB Physical Security (Don’t insert in workstations)
- Employee Responsibility & Accountability
- Company Security policy
- Acceptable Use Policy
- Expect actions to be monitored
- Where can I receive more information
- What email address to report incidents (Your Security group email)
- What number to call if I have questions
- Q&A – Questions & Answers
In addition to your PowerPoint presentation, ensure that you have printed media available to hand out to your employees so they can take it home. Here are some useful ones: (additional ones are available here at SANS: Securing the Human)
Let’s now cover the Security Awareness Training topics in detail:
1. Basic Terminology
Just as you would start with the ABCs, you should also cover some security terminology so your employees know the meaning when they hear it on the media or newspaper.Explaining the CIA Triad (Confidentiality, Integrity, and Availability) and tying them to real-world concepts will help your employees understand the purpose of Security clearly.
Example:
- Confidentiality – Ensuring that your Health records are only read by doctors who have a need to know about the data.
- Integrity – Ensuring that financial & accounting records are not modified in any way.
- Availability – Ensuring the up-time of company operations so we don’t lose money (Drilling operations, Restaurant operations, etc)
2. Sensitive Data
As mentioned earlier, you should really understand the nature of your business, and then talk specifically about your industry first. If you are in the healthcare industry, ensuring that HIPAA is covered and PII (Personal identifiable information) is also part of the conversation. Always relate this information to their personal lives (Such as Social Security #, Driver license, Bank account information). People will care if it directly impacts them!
3. Cost of Breaches
You may cover various things such as the cost of a credit card being sold on forums. Costs associated with breaches such as (Remediation, Loss of customers, Business disruption, Regulatory Fines (HIPAA), Legal costs, Public relations, Breached client records, Notification costs, Identify monitoring and repair, etc..)
Secondly, cover breach facts that include how breaches occur such as the negligence or unintentional behavior of employees. Talk about how long it usually takes an incident to be detected, and how most incidents occur because of weak, default, or stolen passwords.
4. Examples of Breaches
Talk about past and current breaches, specially those in your sector, or those that people recognize easily.
5. How to protect your company
As I mentioned before, some of your employees have different reasons to attend your security awareness training. Some of them want to take valuable information back home and use it; therefore, this is an area where you can provide recommendations such as:
- Using password managers – Examples (LastPass, Dashlane)
- Two factor authentication – DUO, Google 2 step verification, etc.
- Backup solutions – Dropbox, Box.com, Google Drive, OneDrive.
(Note: Provide employees with a printed version of this)
6. Attacks
I found that videos are a good way to explain attacks to employees. I personally like the SANS: Protecting the human series which can be accessed here, A 2-4 minute video will be more than enough to relay this information. As I mentioned before, the key takeaway of my presentation was to make employees more aware of phishing; therefore, a majority of time was spent on phishing examples and what employees should look for. Some items covered were:
- Traditional E-mail examples – Screenshots of bank emails
- Real E-mail examples that I collected over 6 months (Included Subject lines such as:
- Office 365 Activation,
- Invoice #1234.pdf,
- X user has shared a file with you [Dropbox,OneDrive,GoogleDrive]
- Verify your recent activity
- Delivery Status
- Screenshot of multiple “Enable macros” messages on emails
- Screenshots of Fedex, UPS, IRS, etc..
- Emails coming from trusted vendors, or companies that employees are familiar
7. Phishing Quiz
For the phishing quiz I wanted it to be interactive; however, if you have more than 20 people in one room, this might not work as well as intended. Additionally, some people will be shy or feel that they will get the answer wrong, so participation might vary. Luckily I found a solution for this issue called “PollEverywhere“. You can get 25 free licenses to start off with which is more than enough for a small class. This solution allowed me to present screenshots of “Potential Phish” emails, and by using an app in their phones, they could vote whether they thought it was a real email or fake email.
Here’s an example of a slide used for this quiz:
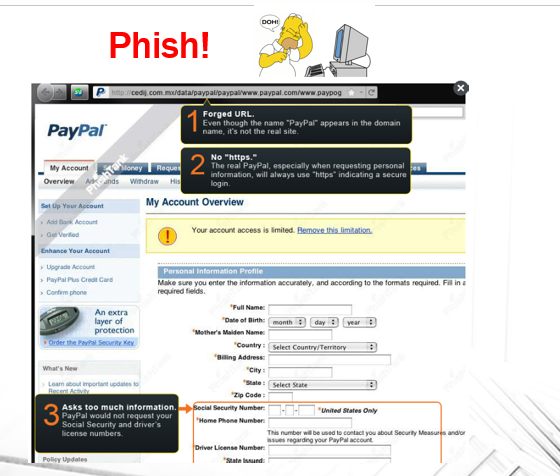
The images were taken from this handy Phishing Quiz by OpenDNS.
Employees loved this exercise as it was fun and interactive. This also allowed me to get the attention of those who had drifted away during the initial part of the presentation.
8. Physical Security
This section is pretty self explanatory; however, you want to ensure that you make a clear point about Physical Security being the most important security. One analogy I provided was “If you give the keys to your home, then there’s no need to break into your house”.
9. Employee Responsibility & Accountability
As mentioned earlier, most breaches occur due to employee negligence or unintentionally clicking on things without thinking about the consequences. This is where you enforce this and clarify that there are consequences to employee negligence. Keep in mind that this all depends on what your written policies are, and if you have message banners when employees login stating that “their actions will be monitored”. Remind employees that if they signed an Acceptable Use Policy, there may be serious consequences of misusing company assets and resources. Personally, at the end of the day, if you can somehow relate this to their personal lives, employees will be more careful about their actions.
10. Where can I get more information
This is the last slide in which you provide your teams’ contact information in case someone needs to report a suspicious email or just has questions about it.
Q&A
Ensure that you allocate some time for employees to ask any questions or if they need clarification on one of your slides. This is very important as people tend to have the same questions but some might not want to ask themselves.
Follow up: Survey
After your security awareness training presentation a survey should be sent to the attendees. This will provide with important feedback about the content of your presentation, as well as if the audience understood your intended message. My recommendation will be to compile a list of questions and list them in a (Strongly disagree, Disagree, Neutral, Agree, Strongly Agree) format so the employees can easily go through them. This should take them 2-4 minutes to complete.
At the end of the survey you should provide additional questions in an Open-ended format the following:
What topics covered will provide you with the most benefit
What did you like about the course?
What did you dislike about the course?
Please write any additional comments below
I used Surveymonkey which worked great!
Reviewing feedback data
Your initial presentations will probably have a handful of feedback; therefore, don’t ignore it! Use this to improve your presentation and modify/add/remove content if needed.
Here’s some of the things I learned from reading user’s feedback and the improvements made:
| Feedback | Improvement |
| Not able to see Phishing examples clearly | For future presentation I used larger visuals and zoomed in as we went through each phishing exercise. |
| Could not hear correctly | Added a Microphone |
| More Examples at home | Included more personal examples that employees could relate to |
| Department Specific Examples | Included vendor logos, examples of targeted phishing emails for Accounting,HR,Finance, etc. |
Do take into consideration that some people might have certain disabilities, including hearing or visual problems; therefore, always have a printed copy of the presentation in case someone needs to follow it that way. I also learned that for some folks, the message doesn’t get across; so having multiple ways of providing that same information is very helpful as it will “click” for them one way or another. Point of this is NOT to assume that everyone learns the same way.
Conclusion
I hope this post helps you create your own Security Awareness training or at least gives you some ideas on the content to add or lessons learned. As you may or may not agree, the human link is the weakest link; therefore, we need to protect it. On the other hand, the human link can be the strongest link and can be an extra set of eyes for your organization.
Things to consider regarding Security Awareness training:
- If you can’t sell it to upper management, it will not succeed – Ensure this comes from upper management to ensure employee cooperation.
- Some employers or employees might see this as a waste of time – You can always do this training as a “lunch and learn” or provide other incentives to get them on your class.
- People will continue clicking on phishing emails – This is a reality; however, you will see an increase in users reporting suspicious emails which is a great improvement!
- Some people will not be able to attend,Period! – Make your presentation into a video or provide a copy of your presentation over email, don’t leave anyone out!
TLDR or Too Long Didn’t Read:
- Security Awareness Training should be a priority
- What should employees get out of your presentation
- Suggested topics for your presentation
- Sensitive data, cost of breaches, Attacks, How to protect your organization, Employee Responsability & Accountability, Physical security.
- Provide Physical media (Such as SANS Secure the Human ). And also useful links for the employee to apply at home.
- Interactive Phishing Quiz for employees using PollEverywhere iphone App.
- Collect employee feedback to improve future presentations
- Alternative ways to get employees to attend your presentation
Thanks for reading!

Nice one, keep me informed.