Here’s a way to deploy Sysmon to all of your domain endpoints using Group Policy.
Step1: Create sysmon install batch file
First create a batch file that will be placed on the root domain folder that is accessible to each domain client.
Here’s the batch file:
if not exist "C:\windows\config.xml" ( copy /z /y "\\domain.com\apps\config.xml" "C:\windows\" ) sc query "Sysmon" | Find "RUNNING" If "%ERRORLEVEL%" EQU "1" ( goto startsysmon ) :startsysmon net start Sysmon If "%ERRORLEVEL%" EQU "1" ( goto installsysmon ) :installsysmon "\\domain.com\apps\sysmon.exe" /accepteula -i c:\windows\config.xml
save as Sysmon_install.bat
What does it do?
The script will copy the sysmon configuration file (config.xml) file to “C:\Windows\” and then if sysmon isn’t running, it will install it using that configuration that we copied.
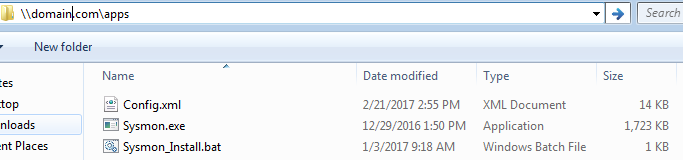
Step 2: Create a folder on your domain that will be replicated with other domain controllers (in my example: apps), and copy the following:
- sysmon.bat
- sysmon.exe (https://technet.microsoft.com/en-us/sysinternals/sysmon)
- config.xml (This is the configuration file that will be used by sysmon when you first deploy it, you may use SwiftOnSecurity’s own configuration to get you started)
Now that you have the prerequisites, let’s move on.
Step 3: Creating a Start-up script
Launch your group policy utility and perform the following:
Right click your domain OU and
- Create GPO in this domain, and link it here
- Provide a name (Sysmon Deployment) , hit OK
- Right click your newly created GPO Sysmon Deployment and select Edit
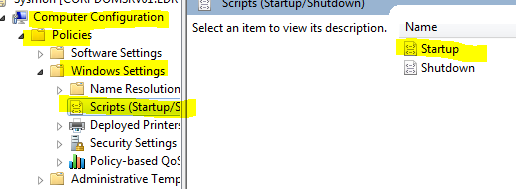
- Navigate to Computer configuration > Policies > Windows Settings > Scripts > Startup
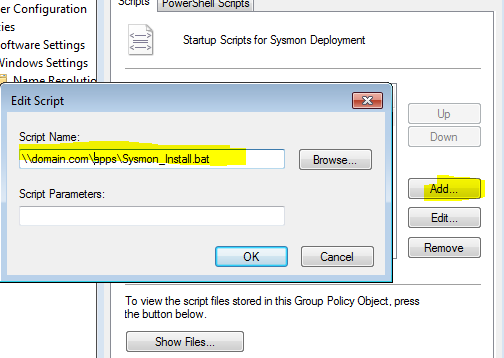
- Click on Startup and Add and browse to your script location \\domain.com\apps\Sysmon_Install.bat and finalize with OK
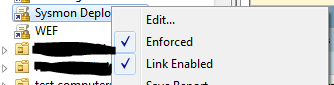
- Right click your newly created GPO and ensure that it’s enabled and enforced (if necessary)
This is it!
The Startup script will run as SYSTEM which should take care of the admin requirements for Sysmon.
Suggestions:
Create a test OU and move a limited amount of endpoints there to get started. Assuming that you already have a log collector, review the type of logs you are receiving and modify your configuration file to include/exclude certain logs so it won’t be overwhelming.
A challenge I came across was updating the configuration file across endpoints. If you were to update your configuration file, the change will only happen once the endpoint refreshes their group policy (defualt is 90 min) or longer at times.
Update September 2017: Preferred method
The previous method above will only deploy this GPO if the client machine is rebooted not just logged off/on thus the term “Startup script”; however, you will soon realize that NOT all of your workstations & servers are rebooted, (specially those production servers in your environment which are never touched). To ensure that we have 100% compliance with our Sysmon deployment, and also a way to automatically update our Sysmon Configuration file here’s an alternative solution which leverages the Scheduled task for Windows.
What will this accomplish?
- Deploy Sysmon along with Initial Configuration
- Check for configuration updates every hour (During Business hours) on an hourly basis.
Step1: Create sysmon install batch file
First create a batch file that will be placed on the root domain folder that is accessible to each domain client.
Here’s the batch file. (This file will always write to C:\Windows and replace whatever configuration file is already there)
copy /z /y "\\domain.com\apps\config.xml" "C:\windows\" sysmon -c c:\windows\config.xml sc query "Sysmon" | Find "RUNNING" If "%ERRORLEVEL%" EQU "1" ( goto startsysmon ) :startsysmon net start Sysmon If "%ERRORLEVEL%" EQU "1" ( goto installsysmon ) :installsysmon "\\domain.com\apps\sysmon.exe" /accepteula -i c:\windows\config.xml
Step 2: Create a folder on your domain that will be replicated with other domain controllers (in my example: apps), and copy the following:
- sysmon.bat
- sysmon.exe (https://technet.microsoft.com/en-us/sysinternals/sysmon)
- config.xml (This is the configuration file that will be used by sysmon when you first deploy it, you may use SwiftOnSecurity’s own configuration to get you started)

Now that you have the prerequisites, let’s move on.
Step 3: Creating a Scheduled Task
Launch your group policy utility and perform the following:
Right click your domain OU and
- Create GPO in this domain, and link it here
- Provide a name (Sysmon Deployment) , hit OK
- Right click your newly created GPO Sysmon Deployment and select Edit
- Navigate to Computer configuration > Preferences > Scheduled Tasks
- Right click Scheduled Tasks and click on Scheduled Tasks (At Least Windows 7) (This should work for Windows 7,10 Server 2008/2012)
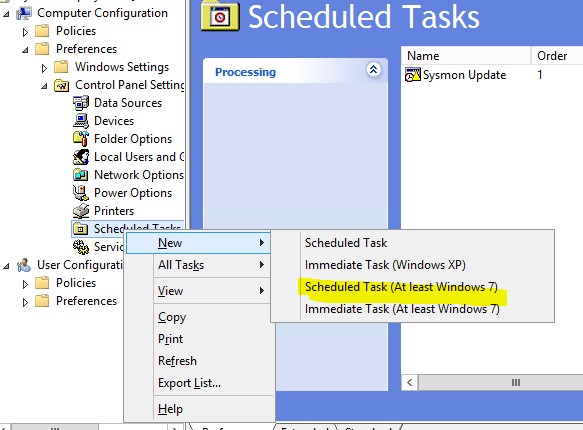
6. Under the General Tab set the following:
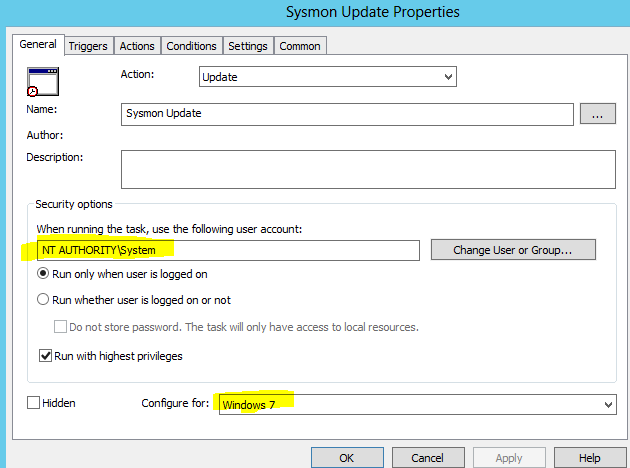
7. Under the Trigger Tab click on New
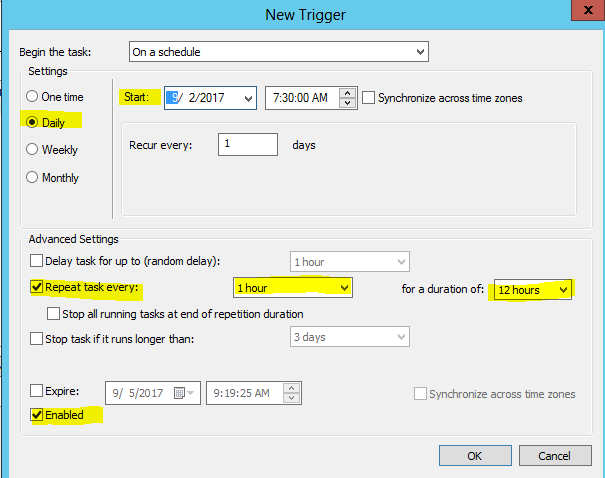
Hit OK when done.
(This will check your sysmon configuration every hour after 7:30 a.m, until 7:30 p.m, set to your own production hours when you expect to make changes to your sysmon config). This will allow all of your clients to constantly check for an updated version of sysmon config. This is helpful when you have hundreds or thousands of systems and you need a way to deploy the same configuration file.
8. Under the Actions tab click on new
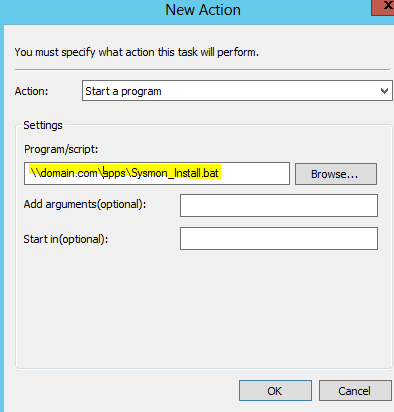
Browse to your sysmon.bat file and hit OK when done.
9. Optional step: Under the Settings tab, you can check the
Allow task to be run on demand (This will allow you to manually trigger the scheduled task on an endpoint when you login. It helps with initial testing).
10. Once done, click OK.
You should now see your task created.
Exit out of Group Policy.
Now you will be sure that all of your endpoints are installing sysmon and checking for updates.
Final Notes:
- You can probably add a condition to check for file size differences or similar so your endpoints won’t continue grabbing the same configuration file if it never changes.
If you have any questions feel free to send me a message on Twitter where I’ll answer quicker.
Updated the batch script to check for differences in the config before pulling it.
@ECHO OFF
fc c:\windows\sysmon\config.xml “\\domain.com\apps\config.xml” > nul
If “%ERRORLEVEL%” EQU “1” (
copy \z \y “\\domain.com\apps\config.xml” “C:\windows\sysmon”
sysmon -c c:\windows\config.xml
sc query “Sysmon” | Find “RUNNING”
If “%ERRORLEVEL%” EQU “1” (
goto startsysmon
)
:startsysmon
net start Sysmon
If “%ERRORLEVEL%” EQU “1” (
goto installsysmon
)
:installsysmon
“\\domain.com\apps\sysmon.exe” /accepteula -i c:\windows\config.xml
[…] is a script from “Deploying Sysmon through Group Policy (GPO)” and the […]
Hi Pablo, Thanks for putting together an amazing article on deploying sysmon on enterprise level. I am currently testing this with my testing environment which consists of WinServer2012 (DC); win10; win8.1 and win7 workstations. I followed your guide by creating a GPO for scheduled Task where NT AUTHORITY\System will execute a sysmon install script on a share. The issue I am having is that sysmon is installed on all the machines except win10. I think it may be to do with the permissions that NT AUTHORITY\System has to the network shares or the sharing permission of the share where the… Read more »
What happens if you run the Sysmon installer manually on one of those Windows 10 endpoints? You mentioned Sysmon is installed on all other endpoint systems except Windows 10; therefore, I’d assume that the other endpoints would have the same permissions issue with the network share as well.
Hi Pablo, Thanks for the reply. So let me explain and take you through the things that I attempted. When the GPO was set from the DC, I did ‘gpupdate /force’ on all the client workstations to apply the group policies. I then looked at the Scheduled tasks and the Sysmon install task was present (which tells me that the GPO was applied correctly on all workstations). After the Scheduled task was triggered on time, I checked all the workstations to confirm whether Sysmon was installed or not. Surprisingly, Sysmon installed on win7 and win8.1 fine but not on win10.… Read more »
Hi Pablo,
I was thinking about ways an attacker could possibly leverage the scheduled task and use it as privilege escalation.
Do you think an adversary could possibly leverage the scheduled tasks running as NT AUTHORITY\System on the workstations?
For example, maybe replace the Sysmon.exe with an evil.exe where local system account will install that evil.exe on the workstations from the scheduled tasks?
Please let me know your thoughts on this. I don’t know if this is possible, but would it be good practice to run the task as local system?
Temp111,
Just wanted to share some of my thoughts. The answer to this is yes, but you can take protective measures. You want to ensure that the “Sysmon.exe” is in a share folder with read only rights. This will ensure that no normal users can modify this file or any other files. Only administrators should be able write to this share. With that said, if an adversary were to obtain admin rights to modify the file, at that point they would be able to do much more.
Thanks for sharing.
Anyone using a x64 version of Sysmon, please remember to adjust the script accordingly.
[…] The SysPanda article here details the process: https://www.syspanda.com/index.php/2017/02/28/deploying-sysmon-through-gpo/ […]
Altered the script to check if both config file and sysmon.exe are up to date.
@ECHO OFF
fc c:\windows\sysmon_config.xml “\\domain\scripts\sysmon\sysmon_config.xml” > nul
If “%ERRORLEVEL%” EQU “1” (
copy \z \y “\\domain\scripts\sysmon\sysmon_config.xml” “C:\windows\”
sysmon64 -c c:\windows\sysmon_config.xml.xml
)
fc c:\windows\sysmon_config.xml “\\domain\scripts\sysmon\Sysmon64.exe” > nul
If “%ERRORLEVEL%” EQU “1” (
goto installsysmon
:installsysmon
sysmon64 -u force
“domain\scripts\sysmon\sysmon64.exe” /accepteula -i c:\windows\sysmon_config.xml
)
sc query “Sysmon64” | Find “RUNNING”
If “%ERRORLEVEL%” EQU “1” (
goto startsysmon
)
:startsysmon
net start Sysmon64