I’ve been using Sysmon for quite some time now and it has made my life much easier when hunting for unknown processes or looking for outbound connections.
My use case
It’s overwhelming looking at your web filter solution and seeing the amount of connections that are established to the internet daily. As you become familiar with your Layer-7 firewall or other fancy web-filter you’ve most likely have learned to filter the traffic to specific categories such as (Unwanted software, P2P Network, Unknown or newly registered domains, etc.) and focus on those.
The problem becomes this, when looking at suspicious connections, we know a few things. The source IP, and Destination IP address, and port #; however, we don’t know exactly what is triggering these connections. This is where Sysmon becomes very useful.
Here’s an example: Outbound connection to adobe.com coming from my local computer (screenshot below is from my web filter). I don’t recall having visited that site at all; therefore I’d like to see what process is making this connection.
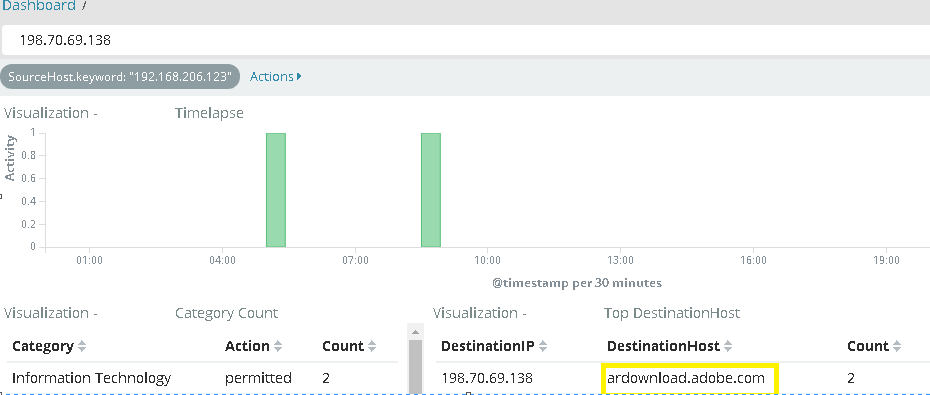
We then look at event logs and find the appropriate Sysmon event log.
Here we can find the process that is making the connection to the IP address of 198.70.69.138 which we know is going to ardownload.adobe.com. As you can see this is coming from C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe
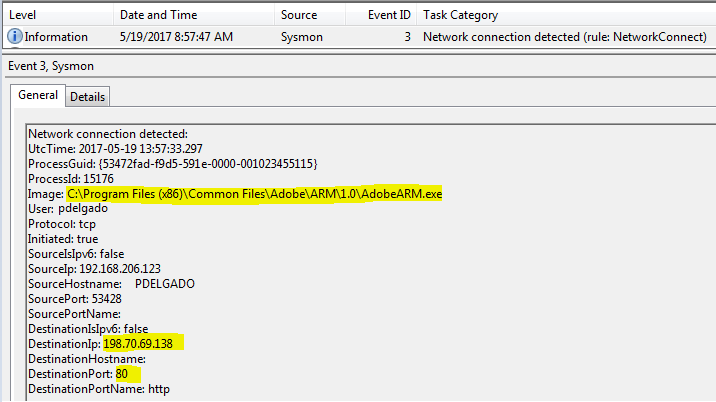
As I mentioned earlier, Sysmon can give you visibility on potentially malicious processes on all of your endpoints. Now, with regards to domain or workgroup endpoints, you may setup Sysmon + Winlogbeat + Elasticsearch to collect endpoint logs real-time and thus see all network connections being generated.
Hunting for Malicious processes:
The process winwb.exe was unknown to me and I saw that it was calling out multiple IP addresses which raised a red flag.
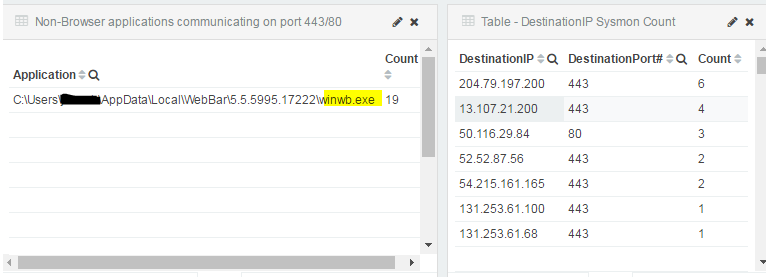
After finding the executable name, I was able to UNC to the system and get a file hash which I then compared to virustotal.com
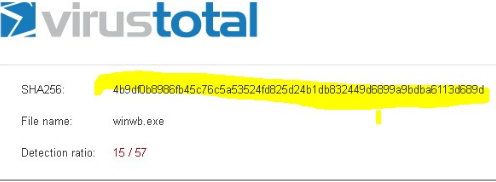
This was a Potentially Unwanted Program (PUP), therefore it was removed from the system. As you can see Sysmon provides useful information on processes calling outbound to potential Command and Control servers (C2C); therefore, it is important to send these endpoint logs to a centralized location and ensure that you have a way to visualize them to spot any strange connections being made.
Part 2 of this series will go over adding threat intelligence to your outbound IP address data to find known Command & Control (C&C) addresses.
[…] Part 1: Detecting Outbound Connections – Basic write-up on how sysmon can detect application callbacks and may be used to find malware running on systems. […]