I’ve been using Sysmon for about 2 years now and it’s one of my favorite Sysinternal tools. My use-cases include and are not limited to the following:
- Finding unknown & potential malicious processes running
- Identifying the source process of outbound connections
- Registry modifications (add/modify/delete)
- Recording Command/Powershell commands ran in my endpoints
If you’re visiting this site, chances are that you’re already familiar with the vast logging of this tool; otherwise, if you need a more in depth introduction and what this tool can do, you may visit the Sysinternal site for more information.
Getting Started with Sysmon
Step 1: Setup Sysmon (Note: This will apply to Sysmon 5.02 and version 6)
Download Sysmon from here: https://technet.microsoft.com/en-us/sysinternals/sysmon
1. Extract to a local destination
2.Launch a command prompt with elevated privileges (right click-run as Administrator)
3.Run the following command: Sysmon.exe -I -h sha256 -n /accepteula
4.You should then see a message similar to the screenshot below, and eventually see the service Sysmon getting started.
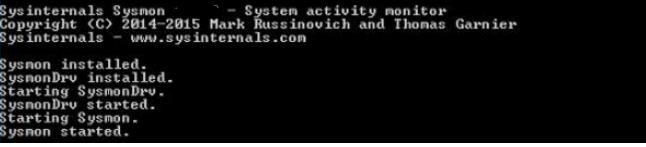
5. Verify that sysmon is running by going to windows services. 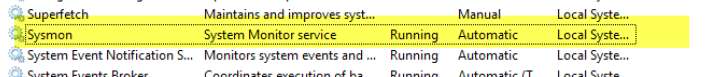
You may now launch your Event Viewer
Navigate to > Application and Services Logs > Microsoft > Windows > Sysmon > Operational
You will see hundreds of logs being generated by your system which will include processes being created, modified, network connections, etc such as those shown in the following image:
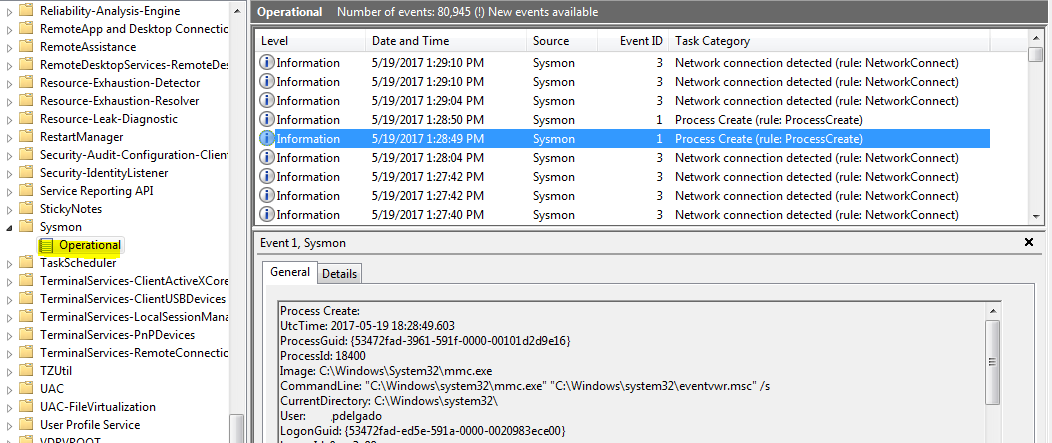
Step 2: Keeping important logs & Discarding chatty ones
As you already saw, Sysmon will generate a tremendous amount of logs. If you decide to install and collect all of your domain endpoint sysmon logs, you will need to filter out the “Noise”; however, you also don’t want to filter out everything since you want to collect important forensic data that might be useful in a potential breach.
Here’s a simple configuration that I created that you may get started with.
I have commented the Event IDs so you may double-check what we’re doing.
Copy the following and paste it in notepad (or your preferred text editor) and save it as config.xml
Update September 2017: For Sysmon 6.1 you might need to change the schemaversion to version 3.40 <Sysmon schemaversion=”3.40″>
<!-- Reference to the logs below https://technet.microsoft.com/en-us/sysinternals/sysmon -->
<Sysmon schemaversion="3.20">
<!-- Capture SHA256 -->
<HashAlgorithms>SHA256</HashAlgorithms>
<EventFiltering>
<!-- Event ID 1: ProcessCreate -->
<ProcessCreate onmatch="exclude">
<IntegrityLevel>System</IntegrityLevel>
<!-- Google Chrome -->
<Image condition="Is">C:\Program Files (x86)\Google\Chrome\Application\chrome.exe</Image>
<Image condition="contains">Chrome\Application\chrome.exe</Image>
<!-- Other Chatty applications -->
<Image condition="contains">C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe</Image>
<Image condition="contains">C:\Windows\SysWOW64\Macromed\Flash\FlashPlayerUpdateService.exe</Image>
<ParentImage condition="contains">C:\Program Files (x86)\Google\Update\GoogleUpdate.exe</ParentImage>
<CommandLine condition="contains">C:\Windows\system32\wbem\wmiprvse.exe -secured -Embedding</CommandLine>
<ParentCommandLine condition="contains">C:\Windows\system32\SearchIndexer.exe /Embedding</ParentCommandLine>
<ParentCommandLine condition="contains">C:\Windows\system32\SearchIndexer.exe /Embedding</ParentCommandLine>
</ProcessCreate>
<!-- Event ID: 2 FileCreateTime -->
<FileCreateTime onmatch="exclude">
<Image condition="end with">chrome.exe</Image>
<Image condition="end with">firefox.exe</Image>
<Image condition="end with">outlook.exe</Image>
<Image condition="end with">iexplore.exe</Image>
<Image condition="contains">C:\Windows\system32\msiexec.exe</Image>
<Image condition="contains">C:\Windows\syswow64\MsiExec.exe</Image>
</FileCreateTime>
<!-- Event ID 3: Network Connection -->
<NetworkConnect onmatch="exclude">
<DestinationIp condition="contains">169.254</DestinationIp>
<DestinationIp condition="contains">255.255.</DestinationIp>
<DestinationIp condition="contains">239.255.</DestinationIp>
<DestinationIp condition="begin with">10.</DestinationIp>
<DestinationIp condition="contains">127.0.</DestinationIp>
<DestinationIp condition="contains">0:0:0</DestinationIp>
<!--<Image condition="end with">iexplore.exe</Image> -->
<!--<Image condition="end with">chrome.exe</Image> -->
<Image condition="end with">excel.exe</Image>
<Image condition="end with">winword.exe</Image>
<Image condition="end with">lms.exe</Image>
<Image condition="end with">onenote.exe</Image>
<Image condition="contains">C:\Program Files\Mozilla Firefox\firefox.exe"</Image>
<Image condition="contains">C:\Program Files\Mozilla Firefox\firefox.exe</Image>
<DestinationPortName condition="end with">dhcpv6-client</DestinationPortName>
<DestinationPortName condition="end with">epmap</DestinationPortName>
<DestinationPortName condition="end with">llmnr</DestinationPortName>
<DestinationPortName condition="end with">netbios-dgm</DestinationPortName>
<DestinationPortName condition="end with">netbios-ns</DestinationPortName>
<DestinationPortName condition="end with">netbios-ns</DestinationPortName>
<SourcePortName condition="end with">llmnr</SourcePortName>
<SourcePortName condition="end with">epmap</SourcePortName>
<SourcePortName condition="end with">ws-discovery</SourcePortName>
<SourcePortName condition="end with">ssdp</SourcePortName>
</NetworkConnect>
<!-- Event ID: 5 Process Terminate. We're not logging process termination -->
<ProcessTerminate onmatch="include"/>
<!-- Event ID: 6 Driver Loaded: Log all drivers except if signature Contains Microsoft or Windows-->
<DriverLoad onmatch="exclude">
<Signature condition="contains">microsoft</Signature>
<Signature condition="contains">windows</Signature>
</DriverLoad>
<!-- Event ID: 8 Log CreateRemoteThread -->
<CreateRemoteThread onmatch="include">
<TargetImage condition="image">lsass.exe</TargetImage>
<TargetImage condition="image">winlogon.exe</TargetImage>
</CreateRemoteThread >
<!-- Event ID: 9 RawAccessRead -->
<RawAccessRead onmatch="exclude">
<Image>C:\Windows\System32\wbem\WmiPrvSE.exe</Image>
<Image>C:\Windows\System32\svchost.exe</Image>
</RawAccessRead>
<!-- Event ID: 11 FileCreate -->
<FileCreate onmatch="include">
<TargetFilename condition="end with">.exe</TargetFilename>
<TargetFilename condition="end with">.pdf</TargetFilename>
<TargetFilename condition="end with">.vbs</TargetFilename>
<TargetFilename condition="end with">.doc</TargetFilename>
<TargetFilename condition="end with">.hta</TargetFilename>
<TargetFilename condition="end with">.xls</TargetFilename>
</FileCreate>
<!-- Event ID: 12 Certain registry keys (AutoStart, Services,Debuggers) -->
<RegistryEvent onmatch="include">
<TargetObject condition="contains">Windows\CurrentVersion\Run</TargetObject>
<TargetObject condition="contains">Windows\CurrentVersion\Image File Execution Options</TargetObject>
<TargetObject condition="contains">CurrentControlSet\Services</TargetObject>
<TargetObject condition="contains">Microsoft\Windows NT\CurrentVersion\Winlogon</TargetObject>
<TargetObject condition="contains">Microsoft\Windows\CurrentVersion\Policies\Explorer</TargetObject>
<TargetObject condition="contains">Microsoft\Windows\CurrentVersion\RunOnce</TargetObject>
<TargetObject condition="contains">System\CurrentControlSet\Services\Tcpip\parameters</TargetObject>
</RegistryEvent>
<!-- Event ID: 15 FileCreateStreamHash Events -->
<FileCreateStreamHash onmatch="exclude">
<TargetFilename condition="end with">.directory</TargetFilename>
<TargetFilename condition="end with">.sxx</TargetFilename>
<TargetFilename condition="end with">.partial</TargetFilename>
</FileCreateStreamHash>
</EventFiltering>
</Sysmon>
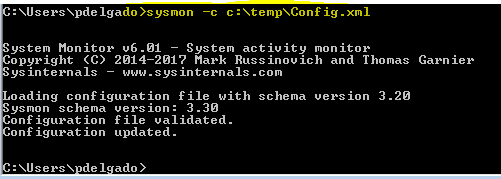
We will launch a command prompt with elevated privileges, and run the following:
sysmon -c c:\thepathtoyourconfig.xml
This command will allow Sysmon to run based on a specific configuration that we’re providing.
Again review your sysmon event logs and continue filtering “normal” process behaviors; however, do read my article called “Advanced Sysmon Filtering” which will explain why we shouldn’t just filter out processes such as svchost.exe, csrss.exe, conhost.exe, services.exe, etc which are often targeted by Malware.
If you don’t have tons of time, you can use SwiftOnSecurity’s xml configuration which may be accessed here . He/she has done extensive research on interesting artifacts to look for, which will get you started; however, it covers a finite amount of logging.
As you can see this tutorial pertains to 1 system only; however, if you are looking to deploy sysmon to hundreds or thousands of endpoints you will need to setup a way to capture these logs real-time.
I would suggest to read the following to setup a centralized log management solution:
- Setting Up Elasticsearch on Centos 7
- Set up Winlogbeats to send Windows Logs to Elasticsearch Or if you have a domain environment you can setup a Windows Event Forwarder server and accomplish the same here
- Deploy Sysmon through Group Policy (If you are planning on deploying sysmon to domain systems)
I will continue writing more Sysmon & Logstash articles to enhance our captured data.