This will be a 3 part series in which we will setup a Windows Event Forwarder server which will collect event logs from Domain-joined Windows workstations based on subscriptions that we create.
This will allow you to collect domain computer event logs real-time (they really are real-time).
Here’s an example of how they would display.
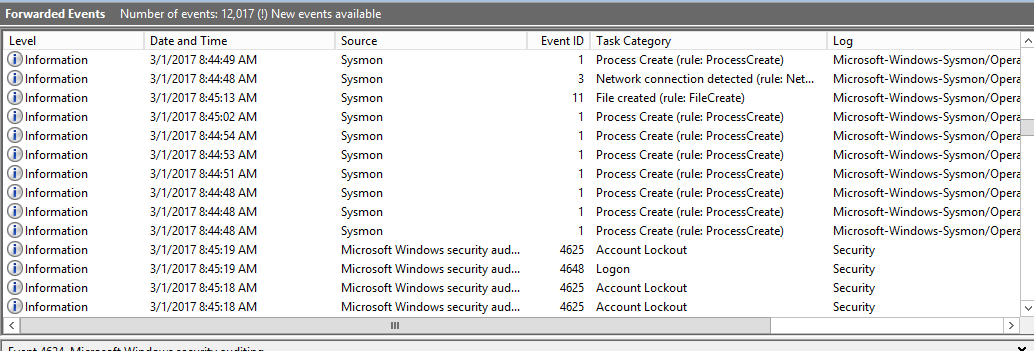
Once you are done with this series, you may want to send your WEF logs to Elasticsearch and visualize them on Kibana as that is our end goal.
Here’s some of your future dashboards
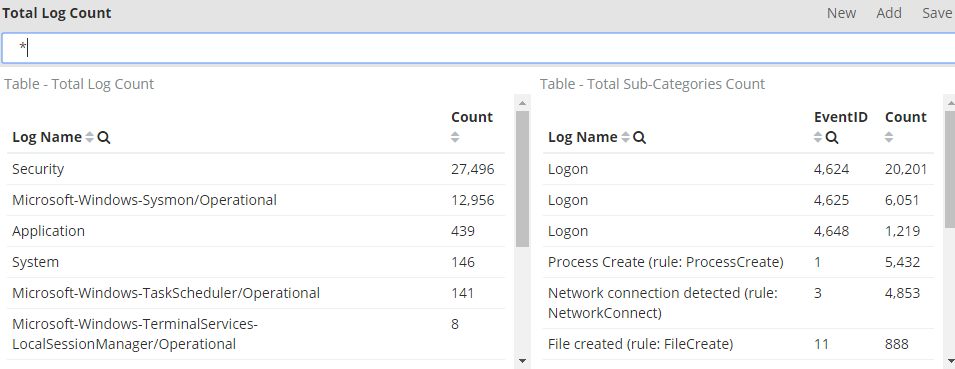
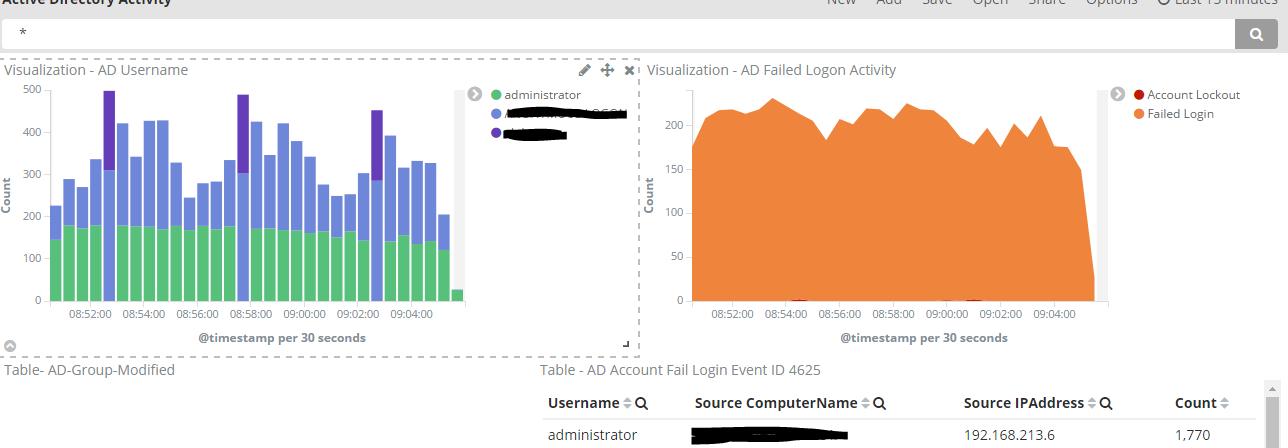
Anyways, let’s get started.
Prerequisites:
- Windows Server for log collection in a domain environment.
- Create a computer group in your domain (my example will be WEF Computers)
Step 1: Setting up WEF
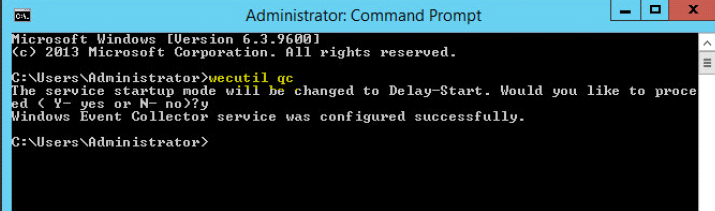
1. Log in to Windows server in this case (WindowsLogCollector)
2. Launch command prompt nad type: wecutil qc
Hit Y to procceed.
(note: Wecutil.exe is a Windows Event Collector utility that enables an administrator to create and manage subscriptions to events forwarded from remote event sources that support the WS-Management protocol.)
Step 2: Setting up Event Subcriptions
1. Browse to Event Viewer
2. Right click Subscriptions and create subscription
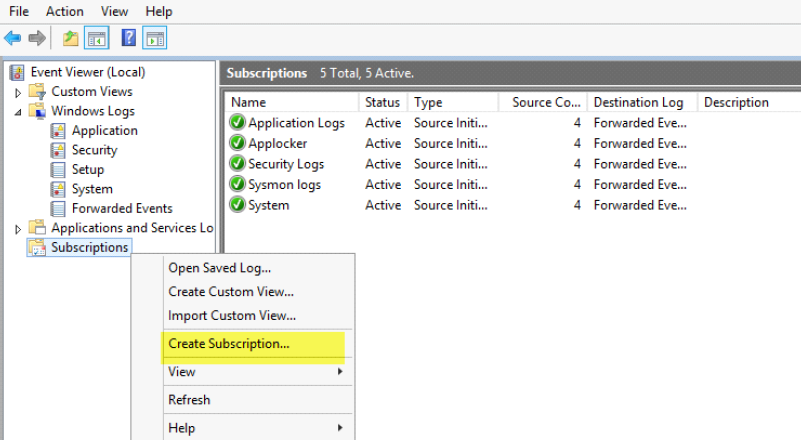
3. Provide a meaningful subscription name (e.g Application, Security, System)
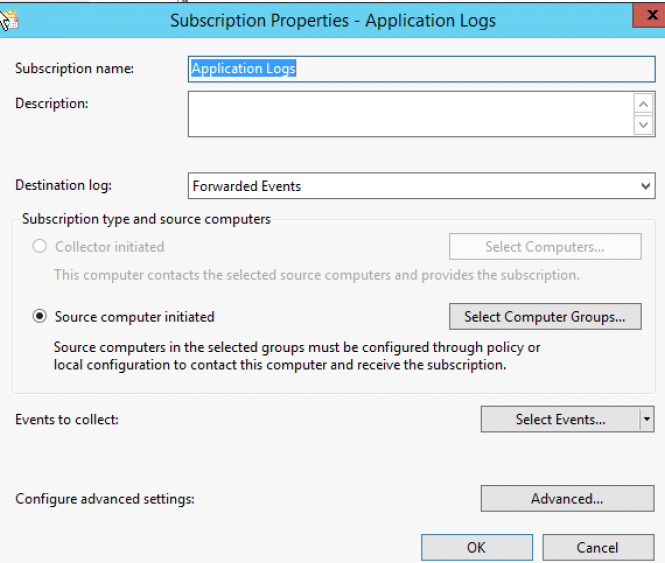
4. Click on Select Computer Groups and add the computer group you’d like to see. In this example I have a computer group called WEF Computers. Now we Add Domain Computers and click OK. (Alternatively, you can add individual systems here as well)
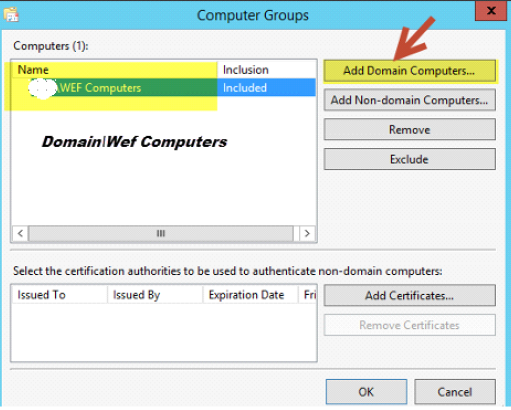
Click “OK” once done.
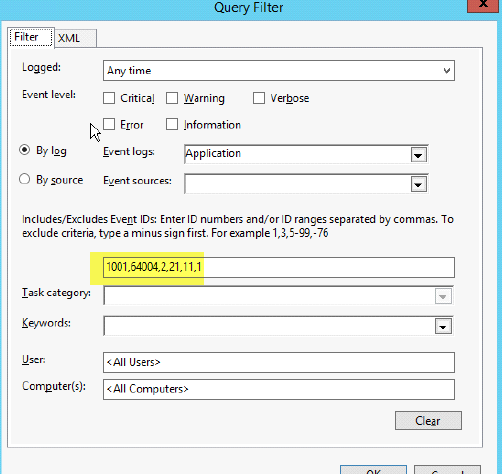
5. Next Select Select Events and choose the type of logs that you want. (note, if you are unsure what logs to get, just check the event level boxes so you may grab all logs). We limited this to a few selected ones that we’re interested in.
6. Lastly, select Advanced and fill in the option Minimize Latency
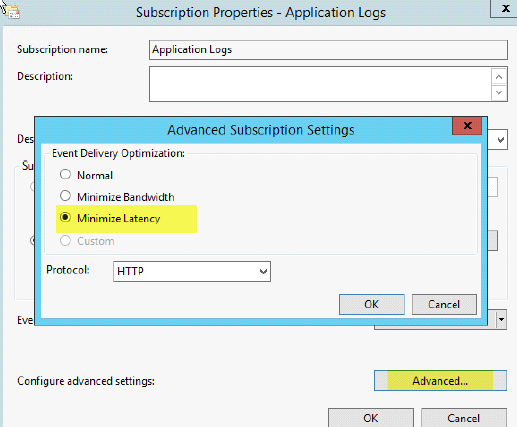
Hit OK
You have now created your first Windows Event Forwarder Subscription. Repeat the steps for other logs such as System, Sysmon (See part 2 of this series), etc.
Not sure what Logs to monitor?
Below is a list of Event IDs along with a description. I have a longer list saved; however, these are the ones I believe should be monitored.
Security Logs:
| EventID | Description | Source |
| 4756 | A member was added to a security-enabled universal group | Security |
| 4740 | A User account was Locked out | Security |
| 4735 | A security-enabled local group was changed | Security |
| 4732 | A member was added to a security-enabled local group | Security |
| 4728 | A member was added to a security-enabled global group | Security |
| 4724 | An attempt was made to reset an accounts password | Security |
| 4648 | A logon was attempted using explicit credentials | Security |
| 4625 | An account failed to log on | Security |
| 1102 | The Audit Log was cleared | System |
| 4624 | An accout was successfully logged on | Security |
| 4634 | An account was logged off | Security |
| 5038 | Detected an invalid image hash of a file | Security |
| 6281 | Detected an invalid page hash of an image file | Security |
Application Logs
| EventID | Description | Source | Log Name |
| 1000 | Application Error | Application | |
| 1002 | Application Hang- Crash | Application | |
| 1001 | Application Error – Fault Bucket | Application | |
| 1 | EMET | ||
| 2 | EMET |
System:
| EventID | Description | Source |
| 104 | Event Log Cleared | System |
| 1102 | The Audit Log was cleared | System |
| 4719 | System Audit Policy was changed | System |
| 6005 | Event log Service Stopped | System |
| 7022-7026,7031,7032,7034 | Windows Services Fails or crashes | System |
| 7045 | A service was installed in the system | System |
| 4697 | A service was installed in the system | System |
| 7022 | EVENT_SERVICE_START_HUNG | System |
| 7023 | EVENT_SERVICE_EXIT_FAILED | System |
| 104 | Event log was cleared | System |
| 6 | New Kernel Filter Driver | System |
Firewall
| EventID | Description | Source | Log Name |
| 2005 | A Rule has been modified in the WindowS firewall Exception List | Firewall | Microsoft-Windows-Windows Firewall With Advanced Security/Firewall |
| 2004 | Firewall Rule Add | ||
| 2006, 2033 | Firewall Rules Deleted | ||
| 2009 |
Terminal Services
| EventID | Description | Source | Log Name |
| 23 | Session Logoff Scceeded | TerminalServices-LocalSessionManager | Microsoft-Windows-TerminalServices-LocalSessionManager/Operational |
| 24 | Session has been disconnected | TerminalServices-LocalSessionManager | Microsoft-Windows-TerminalServices-LocalSessionManager/Operational |
| 25 | Session Reconnection Succeded | TerminalServices-LocalSessionManager | |
| 1102 | Client has initiated a multi-transport connection | TerminalServices-ClientActiveXCor | Microsoft-Windows-TerminalServices-RDPClient/Operational |
After setting up the subscription, not seeing any Source Computers listed in the column. Not sure why.
Hi, is there a way to do step 2.4 except use a computer OU instead of a security group? We could copy our dynamic computer OU to a security group, but then the security group would be static (we’d have to write a PS script or something to continue to dynamically copy over which is not desirable)