Now that you are sending all of your logs to your Windows Event Forwarder, it’s time to forward them to Elasticsearch so we can visualize them in Kibana and make some meaningful decisions based on the data.
Prerequisites:
- Winlogbeat – Download here (64-bit)
- Windows hosts – Your system in which we will be collecting the logs from.
Step 1: Download and extract winlogbeat.zip to c:\program files\ (Should look like the image below)
Step 2: Open the winlogbeat.yml and edit with notepad:
We will add the following under winlogbeat.event_logs:
winlogbeat.event_logs: - name: ForwardedEvents ignore_older: 72h
(Note: This will not include logs older than 3 days).
Next, scroll down until you get to output.logstash: here you will add your logstash server information
output.logstash: # The Logstash hosts hosts: ["elkorlogstashipaddress:5044"] index: winlogbeat
Save the winlogbeat.yml and exit.
Step 3: Install Winlogbeat as a service
Launch Powershell (Run as Administrator) – and enter the following:
cd "C:\Program Files\Winlogbeat" powershell.exe -ExecutionPolicy UnRestricted -File .\install-service-winlogbeat.ps1 Start-Service winlogbeat
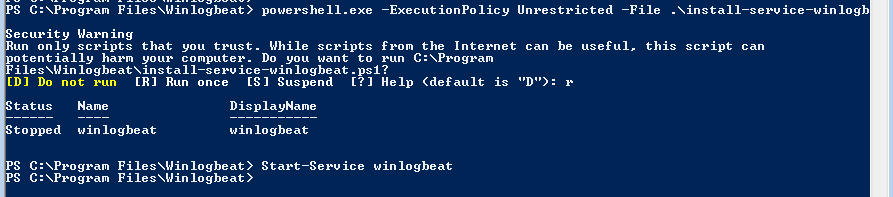
Verify that the service is running.
Done! Next tutorial will focus on Kibana so you may start visualizing the data.
If you have any questions feel free to send me a message on Twitter where I’ll answer quicker.
[…] This means that probably the most efficient way of getting the AZLog events from the central collector to Elasticsearch would be to use WinLogBeat. Configuration is simple enough, simply using a WinLogBeat configuration file like so would do the job [1]: […]
[…] Doku passend für WEC: https://www.syspanda.com/index.php/2017/03/01/sending-windows-event-forwarder-server-wef-logs-to-ela… […]